Some people have the word hackers associated with thieves and cyber criminals. According to our survey among online firms, up to 67% of Slovak and Czech companies have a negative opinion on hackers. This is a consequence of, in particular, negative publicity or, if not, lack of interest in IT security issues, which is also suggested by other survey data.
The survey data shows that up to 48% of local companies do not test their online security at all, even though 44% of Czech and Slovak companies have direct or indirect experience with black hat hackers attack. The same percentage of companies is also unaware that there are more types of hackers and that their ethical hackers can even protect themselves from the attack of malicious counterparts.
Where did the hackers come from?
Hacking as such has been around for nearly 50 years. The first mention of hacking dates back to 1969, when MIT became home to people who were called hackers. Their goal was to improve existing programs to work better and faster. It already indicates that hacking is essentially a positive activity for people who consider themselves specialists in a certain area of information technology.
In nearly 50 years, hacking has gone through various phases of existence. But it was always a good vs evil fight. As the first major hacker of his time we can see John Draper, who “hacked” the telephone network of the US operator AT & T in 1971. At that time, the network was still working on the principle of tonal control.
Draper found out that to make a free call, one has to release a sound with a frequency of 2,600 Hz after reaching the operator. A whistle you could get as a gift in the Cap’n Crunch cereal box at that time made the same sound. Draper seized the opportunity and started producing the so-called blue boxes that reproduced the same sound frequency.

John Draper with a Cap’n Crunch cereal whistle
However, Draper did not believe he was a bad hacker, and justified his “hacker” activities by the interest in operator system itself.
The first mention of evil “black-hat” hackers
In 1983, a year after William Gibson brought the word “cyberspace” to the world, we witnessed the first black-hat hackers attack. Kevin Poulsen, also known as “Dark Dante,” hacked the Arpanet network (which was split in the military and public networks for the first time that same year) and was arrested. He was only 17 years old, so he could not be imprisoned for his act.
Only a year later, the world has experienced the first viruses. Fred Cohen was behind them. In 1984, however, Bill Landreth, also known as The Cracker, was convicted of hacking the computer system and gaining access to NASA and US Department of Defense data.

The current Los Angeles Times supplement, which contained A hacker’s guide to computer security by ‘The Cracker’ (source).
The word cracker thus gained a whole new meaning and began to be used in the “IT-dictionary” dictionary. Today, it is a reference for a person who is aiming to hit a security system with in purpose to cause damage. This is a synonym for a bad or black-hat hacker.
Since 1986, malicious hacking in the form of computer system and network attacks has been defined in the United States as a crime (through The Computer Fraud and Abuse Act).
More references to interesting hacking and IT security events in the world are recorded by SecureList in A brief history of hacking.
You can tell the difference by color
The progressive development of hacking has increasingly divided hackers into various groups – according to their focus. Primarily, they are divided by colors on white, gray and black. In the hacker dictionary, however, expressions like red, green or blue hackers also appear.
White Hat Hackers
The category of white hat hackers includes mainly ethical hackers. Their goal is to recast their hacking capabilities to detect the deficiencies of computer systems, networks, and applications. However, an ethical hacker does this with good intentions, and draws attention to the deficiencies of the owners of the systems under certain ethical principles. Often, for their work, ethical hackers receive a financial reward that motivates them to work further. The bug bounty programs work exactly on this principle.
The history of ethical hacking is linked with bug bounty programs. It began in 1995 when Netscape launched the first public bug bounty program that promised the ethical hackers a reward for finding vulnerability before it could have been misused.
Black Hat Hackers
Black hackers are the opposite of white hackers. They are “bad” hackers (crackers) who try to cause some damage by hacking, or steal the data they sell later on the black market or to your competition. Their primary goal is to make money, regardless of the ethical dimension of the thing.
They do not care who they hack, if they get rich. This is why they are very dangerous . They often choose victims randomly, trying to exploit especially the known security bugs of online systems. Just last year, according to IC3 data, black hat hackers caused damage of at least $ 1.33 billion (but a large number of cyber attacks was not publicly reported).
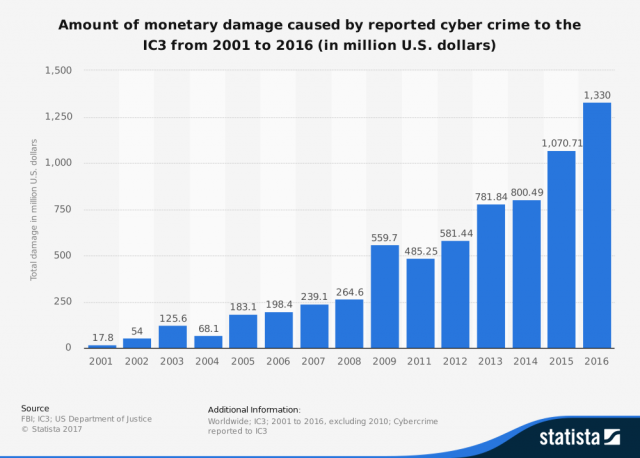
Total damage caused by cyber crime in the US in 2001-2016.
Gray Hat Hackers
Gray hackers fill space between white and black hackers. Their primary goal is not financial gain, but rather entertainment or support of some activity. Often, however, they act outside the bounds of the law.
A special group of gray hackers are hacktivists. Their motivation is social, political or opinional, with cyber attacks often trying to point out some kind of public problem. The word hacktivist was created by a combination of the words “hacking” and “activist”.
More hacking related words and their explanation can be found in the Motherboard’s Cyber Terms and Hacking Lingo dictionary.
Red Hat Hackers
Red hackers are a more radical branch of white hackers. Their goal is the same – to jolt the attack of black hat hackers and to ethically draw attention to security flaws. The difference is that red hat hackers are fighting black hackers with their own weapon – they often try to infect their computers with viruses or attack their networks to destroy their computing resources.
Blue Hat Hackers
The term blue hacker has a specific definition. These are hackers who are in the role of external consultants in companies and apply the techniques used by white (ethical) hackers to find a bug in the system before it runs. This type of hacker is also used by Microsoft to look for bugs in Windows systems, so the specific blue color of Microsoft is used to mark them.
Green Hat Hackers
Green hackers are basically the novices in the area. This term identifies hackers who are the beginners and ask a lot of questions in specialized communities, getting familiar with hacking systems.
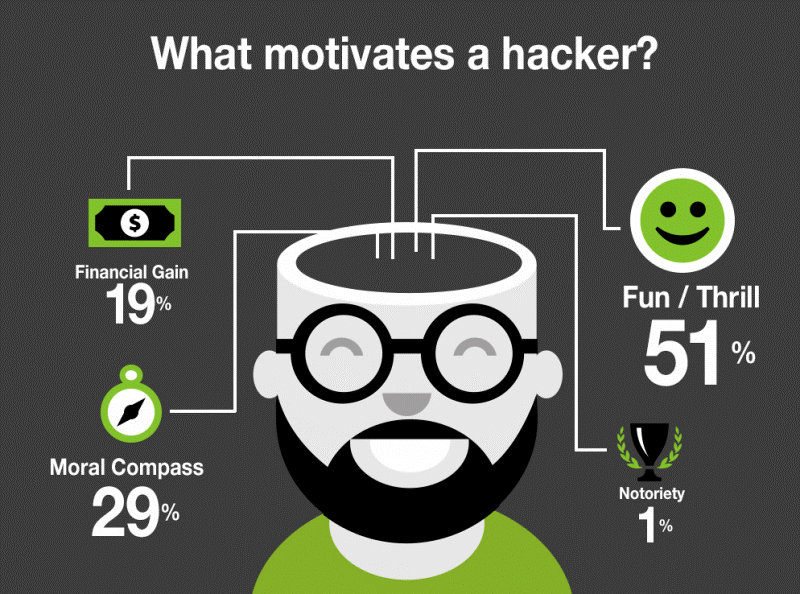
The main motivations of hackers.
Hackers for rent
Hackers are modern criminals, but also security guards. Their job is to test the IT security of computer networks, systems and applications, with every group of hackers trying to do something else. There is one fundamental difference between “good” and “bad” hackers – the option of choice.
While black-hat hackers usually do not care whose system they are going to attack (if they get enough money), ethical or white-hat hackers choose companies that propose them a lucrative offer.
In principle, this really works logically and simply – black-hat hackers attack companies from which they can make the most of, and ethical hackers try to protect these companies because they are offered the money to protect the sensitive data.
So if your company wants to protect its IT system from cyber attack, it should offer a reward for testing IT security and consequent protection of its data to ethical hackers. And this is precisely the purpose of bug bounty program Hacktrophy.