The risk that some black-hat hacker will attack your business increases every year. In Slovakia and the Czech Republic, every sixth company becomes the victim of a hacker attack. Cybercrime targets are different – system disabling, enrichment or theft of sensitive data. But that’s far from being the only consequences of a successful hacker attack. Such attacks lead to high financial loss, which could have often been avoided.
Theft and misuse of business data
Every single day, companies from around the world will lose about 5 million records containing sensitive data due to vulnerability in their system or a human factor failure. Only 4% of escaped data is protected by strong encryption and therefore cannot be misused.
The vast majority of stolen data can be decrypted and ultimately used to gain finances or perform illegal activity. These are login data, payment details, accounting or health records, but also information about products and projects, orders, or partners.
How much do you value these data in your company?
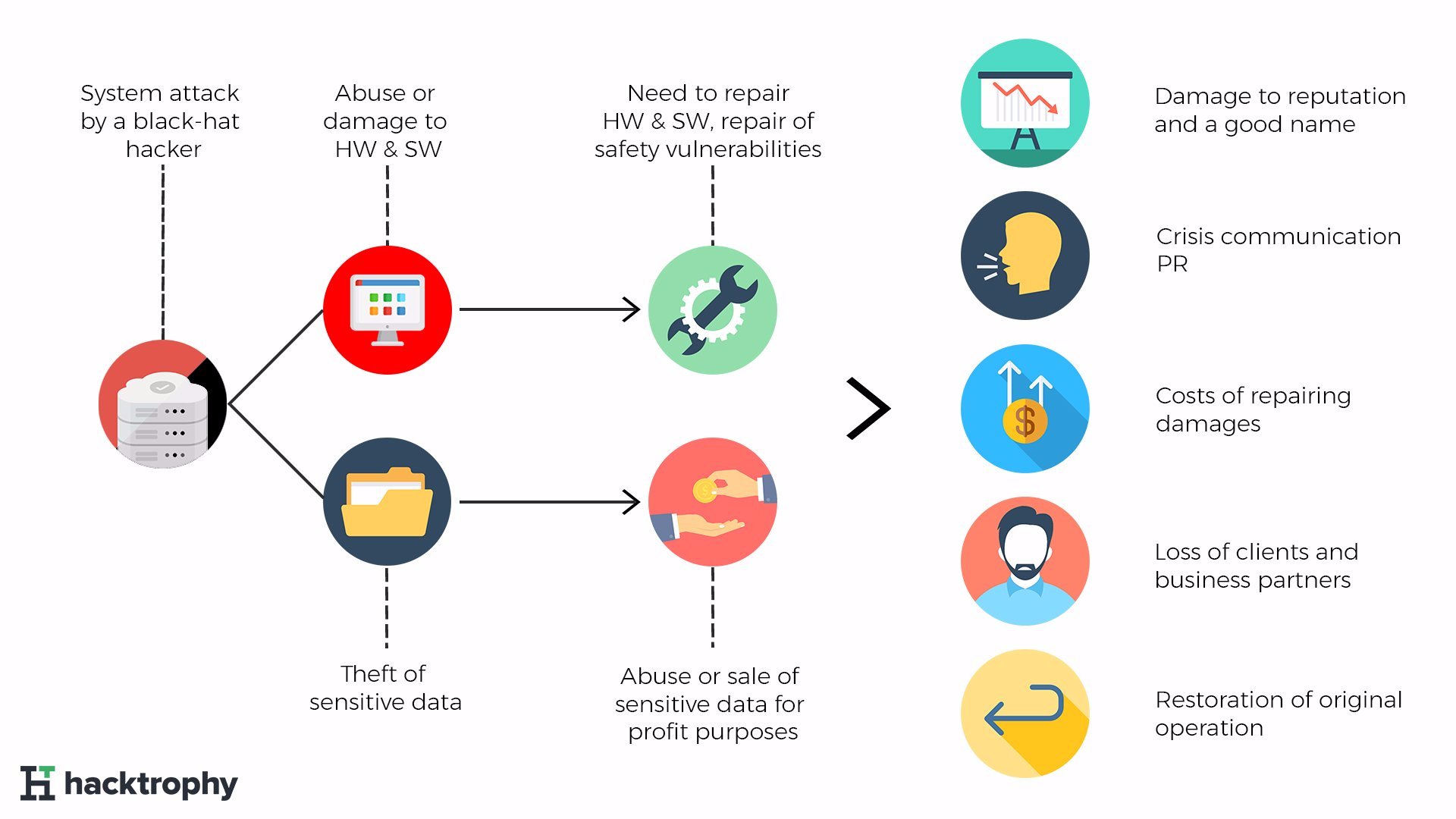
What risks does the company face after a successful black-hat hacker attack?
The latest case of the OnePlus smartphone manufacturer shows the potential consequences of misuse of stolen corporate data. Its servers have invaded malicious hackers who have stolen payment details directly from customers’ Internet browsers. Customers have put the data on the manufacturer’s website when buying one of their products.
In this way, the attackers managed to steal about 40,000 credit card payment data. Although the manufacturer immediately sent an email to affected customers, hundreds of them have already reported misuse of their payment cards. Misusing other stolen data is just a matter of time.
Also the Slovaks and the Czechs have the experienced theft of payment data, illegal cash withdrawals and online purchases. This is most often due to the insertion of payment data into insecure website forms that can be tracked by a black-hat hacker. Often, however, an attacker can also collect payment data from an account he has gained illegally.
Loss of reputation and clients
In addition to the financial impact, the theft of data from companies’ databases may have even worse consequence – damaged reputation, which can result in the loss of business partners and customers.
Hacking of the Czech hosting company Banán s.r.o. in 2010 is another negative example. In addition to data loss, the company has also suffered great damage to its reputation. The attackers first announced the successful attack on the attacked servers and websites, and later they sent an email to the Banán’s customers, in which they warned clients of the lack of security of their hosting.
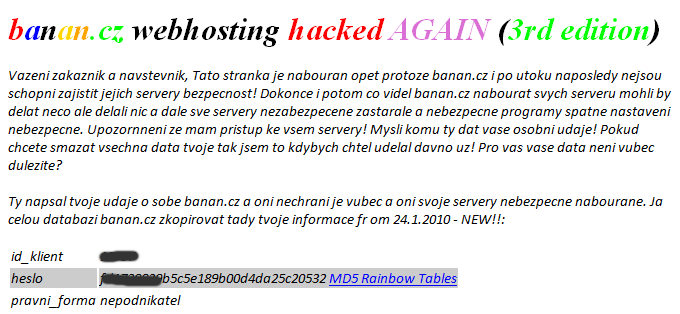
The notification that the hacker displayed on all of the attacked Banan s.r.o.
The result was the loss of a large number of customers who have chosen to use better secured competition. The situation got even worse with the poor crisis communication PR, which talked about “minimal damage despite the theft of data”.
Cost of crisis communication PR
Surveys show that up to 29% of customers in a company that has lost sensitive data will stop using its services. This is a huge number – therefore communication with customers immediately after the security incident is detected, is one of the most important steps to recovery of the damage. It is important to explain how the problem arose and what was done to prevent the stolen data from being misused and the attack not reoccurred. Its goal is to regain customer confidence.
But crisis communication is not cheap or simple and therefore it belongs to the hands of a professional PR agency. Even if the company believes to handle it itself with its own communications department, it is expensive because employees work on agenda different than originally planned and company pays large sums for crisis communication PR publishing. Abroad, the total amount for the crisis communication PR is estimated at hundreds of thousands of dollars, estimated at least a few thousand euros for central european market.
By repairing the safety vulnerability it definitely isn’t over
The fact that a successful hacker attack may cause long-term problems for companies, says, for example, the attack on one unnamed Slovak development company. It was attacked by cyber-attackers only a few months before launching a new project.
The purpose of the attack was to use the company’s server for illegal purposes. As a result of the attack, the company had to postpone the start of the upcoming project. Direct damage was at € 30,000, indirect damage due to damage to reputation was approximately € 15,000. The company had to postpone the launch of the project by 3 months, and dedicate 1 month to repairing the safety deficiencies discovered.
Once the attackers have access to your system, they can exploit corporate infrastructure in several ways. Most often, they are spreading spam or ad emails (if they access the e-mail server), but the misuse of system for DDoS attacks is also quite common. The sale of access data to servers on the black market presents a common tactics.
Most recently, attacked servers are also used to exploit cryptocurrencies, or to long-term spying on communications and to retrieve other sensitive data, or to manipulate the data transmitted. Infection with viruses containing so-called back-doors that allow the attacker to access the system even after repairing the damage caused by the attack and updating the security policy is also a dangerous practice.
The financial impact of the black-hat hacker attack
In the long run, cyber-attacks must also involve increased direct financial expenses. These are needed to repair the hardware and software you are infected with, but also to pay security specialists to help you improve your online protection.
While the amount needed to repair hardware and software is about $ 170,000 in average for larger companies, the total cost of security experts and staff is about $ 200,000 more than during normal business operation. For small and medium sized businesses, this expenses are counted in thousands of dollars.
In addition, you must count on penalties from the state. Since May 2018, the GDPR has also set fines for inadequate protection of sensitive data, up to € 20 million or 4% of your annual turnover. A fine may also be given by your business partners. For example, if you are unable to deliver pre-agreed goods or services because your activity is suspended as a result of hacking.
Accenture has conducted a survey among 254 of its clients who have suffered a cyber attack. Among other things, the survey also refers to the average total “cyber attack price” for 2017, which is at $ 11.7 million. The trend curve is increasing at a relatively fast pace.
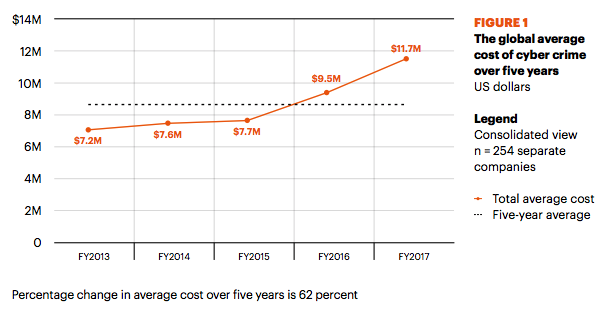
Survey of cyber attack victims’ expenses (source Accenture).
It’s a challenge to return to normal operation
After a successful cyber attack, it is also a common problem to recover the data damaged by an attacker and restart the company’s routine operations. Statistics say that as many as 66% of companies attacked by hackers do not know whether they can still stand on their own feet again.
Even international companies with strong backgrounds often have problems to face the results of hacker attacks. One example of many can be the American financial company Equifax, which last year suffered a cyber attack that meant a loss of sensitive data of 143 million clients. The market price of the company immediately dropped by $ 6 billion, and experts estimate the overall loss to 20 billion. It might as well mean the end of the company.
How to protect yourself?
If you want to protect your data and your company from cyber attacks and huge financial losses, you must regularly invest in your security. Employing a security expert is meaningful, but also relatively costly, being only a first step towards greater security.
The ideal approach is to combine a one-time penetration test with a long-term testing by ethical or white-hat hackers using the bug bounty program. They have the same skills as black-hat hackers, but they follow the Code of Conduct, and especially – they work for you. They will report you the vulnerability found, you will fix it and you pay them for it. The result is a less vulnerable web or application.
Do you want to know more about security testing via Hacktrophy? Read more blogs or go to the How It Works section.


