What are the basic principles of Hacktrophy security testing?
We test everything that is available over the Internet
E-shops
and Websites
Mobile
Applications
Web
Applications
CMS
Cores
Payment
Portals
IoT
Devices
You can test not only the errors caused by the programming or the software used, but also the setup of the infrastructure on which the web or the application is running. Testing can take place in production and test environments.
How Hacktrophy works
You'll pay ethical hackers only for proven errors that actually put your online security at risk.
Learn about real cases of hacked companies around the world.
What a bug bounty program looks like
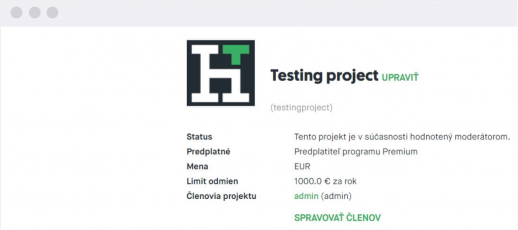
Bug Bounty Program Header
It contains basic information about the bug bounty project – name, status, type, menu, and monthly / annual reward limit for hackers.
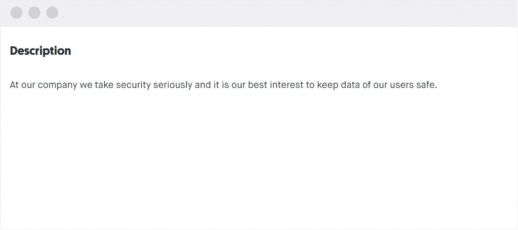
Description of bug bounty program
It works as a short introduction to your company and the tested online project.
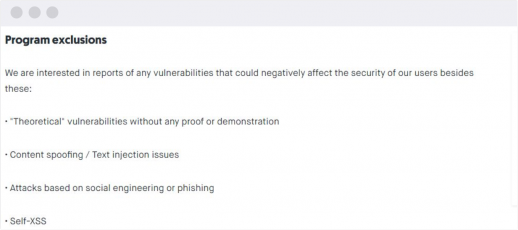
Exceptions from online security testing
Here you specify which types of security vulnerabilities do not interest you and will not be paid for if they are discovered. You can also define forbidden hacker techniques and ways of looking for vulnerabilities.
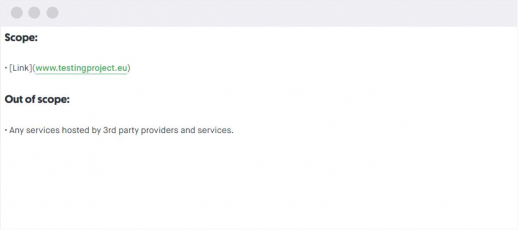
Scope of testing
It specifies which parts of your website, interface, or mobile app should ethical hackers test. They can test in production and test environments, up to your decision.
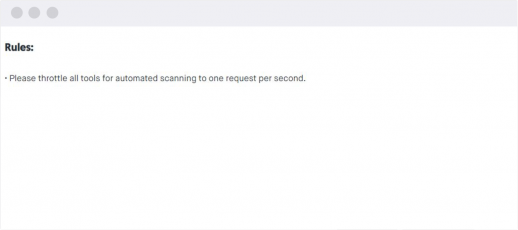
The rules of IT security testing
They allow you to specify rules of security vulnerability search so that you can distinguish our ethical hackers from evil black-hat attackers.
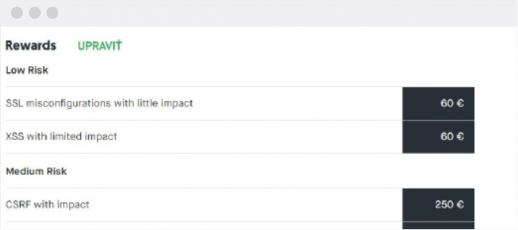
Rewards for ethical hackers
You will display the amount of fees for ethical hackers for discovering relevant security vulnerabilities. We determine them together, depending on the severity of the vulnerability and the program you have purchased.
For download
Download the materials that explain how Hacktrophy's bug bounty works.
Contact an expert
If you're not sure how to use Hacktrophy on your project or you have questions, we'd be happy to help. Talk to Hacktrophy expert.
- Together we will find the best solution
- We help you create a project
- We are on the line throughout the project

