Bug bounty programs bring a unique opportunity to use the knowledge and experience of the community of ethical hackers. They send the reports about vulnerabilities to the owners of the tested systems immediately after finding them. What can you find in this report? How will you work with hackers through Hacktrophy?
The Hacktrophy security report has a standardized structure, regardless of the type of program (package) you use. Its role is to provide the owner of the tested online service (web, mobile application, IoT interface …) as much information as possible about finding the deficiency (usually in the code), its type and placement.
A security report typically includes:
- Type and category of vulnerability
Classification of the vulnerability according to the type of security bug (and to what category of importance it belongs) is based on a vulnerability chart that the company creates in its bug bounty project in advance. An ethical hacker is responsible for the correct classification of the vulnerability in the report, while the Hacktrophy moderator checks the correctness of the ranking.
- Potential reward for the found security vulnerability
It contains information about the amount of a predetermined reward (for a given type of vulnerability) that an ethical hacker will receive once the vulnerability has been confirmed. Rewards for found vulnerabilities are set by the company in advance and ethical hackers perceive them as one of the biggest motivations for finding security flaws in online systems.
- Location of vulnerability
The hacker also reports where he discovered the error. The placement is stated in the form of a URL that refers to the page / subpage of the company, on which the vulnerability is located. The company has the ability to decide which parts of your site or app to test when creating a bug bounty project. So if a hacker reports the vulnerability outside of this assignment, it is up the company whether it pays him a reward. However, if the found vulnerability meets the project bounty conditions and it is valid, the company is required to pay the pre-determined paycheck.
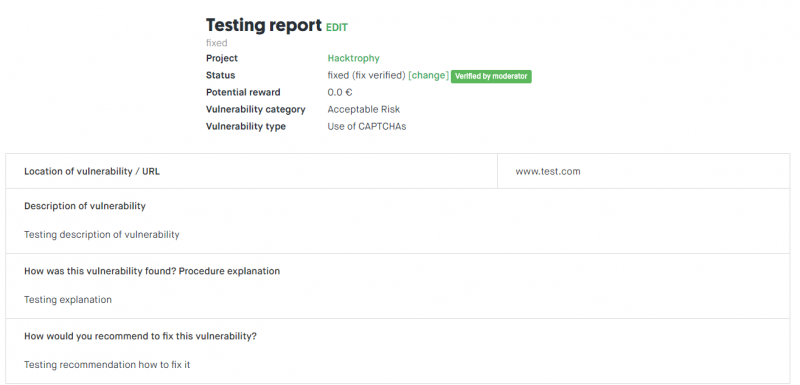
Testing report from ethical hacker in Hacktrophy.
- Vulnerability description
In this box, the hacker tries to best explain what vulnerability is. If possible, the code that contains a security vulnerability will be added to the description of the vulnerability.
- Revelation method
An ethical hacker explains how he discovered the vulnerability. This information will help the owner of the online service or website to fix the vulnerability.
- Recommendation how to fix the vulnerability
If an ethical hacker who has reported a security vulnerability knows how to fix or delete it, he or she may share this information with the owner of the bug bounty project. The author can implement this proposal in the process of removing the reported error. However, this information should be taken as additional. It is true that the online system is best known by its author (architect, programmer …) who can remove the reported error in a different way.
How does the standard vulnerability repair process work?
The status of the report is an important part of the vulnerability report. It varies according to the state of the solution to the safety deficiency. A hacker, as well as a company that owns a bug bounty project, or a assigned moderator, enter the process.
The natural status process, unless the report is canceled by the ethical hacker itself, is as follows:
- New security vulnerability report
The initial state of the report is determined by the owner of the bug bounty program or the assigned moderator. The report can be confirmed or rejected based on its validity and compliance with the published conditions of the bug bounty program. Any unclarity or problems with the reporting can be discussed by the company or moderator and hacker directly in the comments under the report.
- The vulnerability specified for repair
If a bug bounty program owner or moderator (on his / her behalf) receives a message from an ethical hacker, his status may be changed to “GotFix“. This status tells the hacker that his error has been received and is being removed.
- Vulnerability is fixed
You can set the “Fixed” status if the security vulnerability has been removed. We assume that the bug bounty project owner will try to fix the vulnerability as soon as possible. Any controversy can be consulted with the moderator as well as with the ethical hacker directly in the discussion under the report.
- Check of repair
Once the security vulnerability has been corrected, the company may request that the hacker as well as the moderator review the correctness of the repair. Then, the company can change the status of the report to “Fixed (fix verified)“.
- Publishing the report to the public
An ethical hacker, or a moderator, may ask you to publish (report) a vulnerability report. In foreign bug bounty programs, it is quite common to publish fixed vulnerabilities to other software users, so that they can repair them. At the same time, it allows the ethical hackers to build a professional reputation. However, in Hacktrophy, this step is always in full responsibility of the company – the owner of the bug bounty project or the vulnerability. If so, he can do it in the message settings: Edit> Publish.
Upon completion of the reporting “life cycle”, the ethical hacker is paid a reward for finding a vulnerability, and he or she can start searching for other vulnerabilities.
The advantage of bug bounty programs is that companies only pay for real errors that hackers find in their online system. The company will only pay for a real “improvement” of its security. This represents a significant difference from regular IT security firms, where you need to pay a large amount, for example, for a pentest, even if the test does not reveal any security problem.
Testing with bug bounty projects has been used in the Anglo-Saxon world for over 20 years. It is used by large companies as well as medium-sized companies that can not afford costly IT security. If you are considering using the bug program bounty in your company, do not hesitate to contact us, we’d like to clarify further details of Hacktrophy’s operation.


