Are you responsible for the IT security of your company and want to start using Hacktrophy? In the article, you will find tips on how to create your first business bug bounty program.
The main advantage of Hacktrophy bug bounty is the ability to provide accurate, yet complex testing of the safety of your online product. This will be provided by tens or hundreds of ethical hackers who will be interested in your project. Therefore, it is very important for the project to be created correctly and to specify the exact conditions that hackers should follow.
Get started with creating a project for hackers, called a bug bounty program
- The first step you have to do as a company is registering. You can do this by using the button at the top right of the site or in the Login / Registration section.
- After completing all the data in the contact form, check the box sayiing that you want to create a project. Enter its name, your company or organization name, website, and phone number to contact you if necessary.
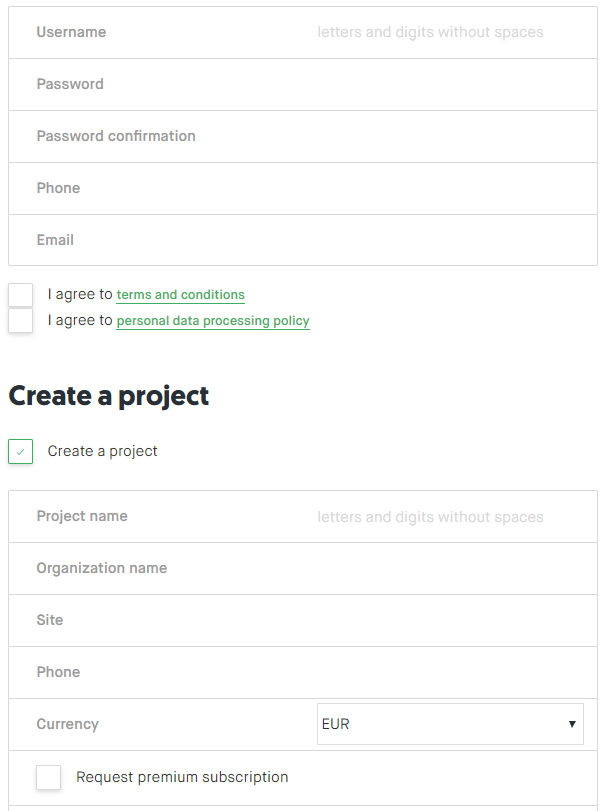
Registration of the company to Hacktrophy.
- If you are not sure how to create and set up your first bug bounty project, go to the Support section or ask our specialists to help you with all the settings and specifications.
- After submitting the project request, you will receive a confirmation email at the address you entered in the contact form. Once confirmed, you are ready to fill out details of your first bug bounty program.
I’ve set my bug bounty program, what next?
- The next step in creating your business bug bounty program is to fill out a questionnaire with 4 questions that help to determine the right amount of rewards for ethical hackers. If you don´t know exactly what vulnerabilities you want to test on your site, no problem, we will help you later.
- Of course, you can adjust the level of rewards anytime in the future. If you don’t know what vulnerabilities you want to focus on, read the Basic Vulnerability Description (PDF in English, Size 50 KB), which contains information about the most common security vulnerabilities you should be interested in. The list is based on the international OWASP methodology.
- After stating all the vulnerabilities you want to test, and rewards for revealing them, you can proceed to the next step. Include the information about your company and a description of the bug bounty program, which should contain, in addition to the definition of the bug bounty project itself, the focus of your company and the conditions that white hat hackers should follow in testing.
- Use our text templates in English language – basic, for larger companies and e-shops, that can be found in the Support section. Setting of a monthly or yearly reward limit is an important parameter, too. The less sure about your security you are, the higher this limit should be.
- The last step you must take is to fill in your company’s billing information. You can add billing information later and save your project as a draft.
Important note: Do not be afraid of this registration process. Later, we’ll give you a security specialist-moderator, and we’ll review each part of the project and we will help you prepare it properly.
How to publish a project for security vulnerabilities search?
Once you complete your company’s billing information, you can submit your project for approval.
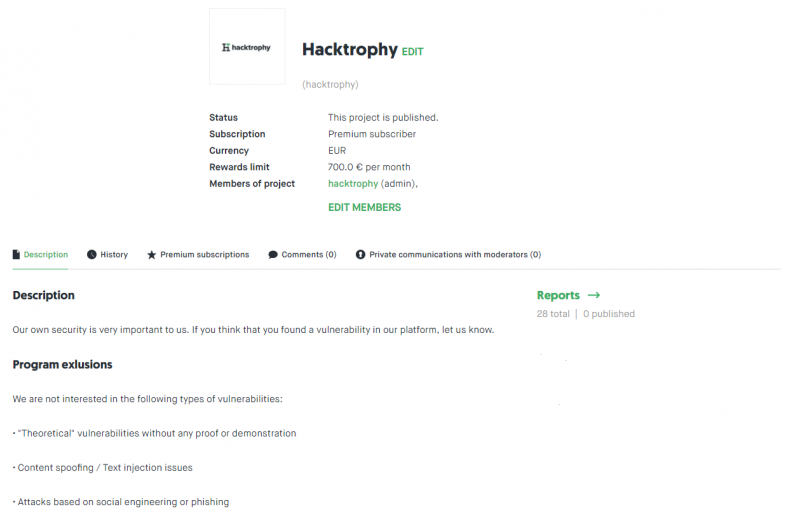
A sample of Hacktrophy’s bug bounty program.


