More than half of all purchases in the world are already happening online. This trend is confirmed by the latest figures from Eurostat – 68 % of internet users in the EU shopped online in 2017. Shopping in e-shops, however, also poses significant security risks on the top of comfort of shopping from home. The article will tell you how to deal with them best.
For e-commerce, nothing is more important than customer trust. A”leaking” website or inadequate security measures, leading to misuse of customer’s payment and / or personal data, may seriously damage the reputation of the e-shop. It is not a little thing – in the last year’s survey, up to 16% of Slovak and Czech companies admitted a direct hacking experience. In the case of leakage of sensitive data of clients, the damaged reputation can cause serious problems also for companies with huge turnover.
That’s why we’ve prepared 20 steps how to improve your e-shop’s security.
-
Choose secure and reliable hosting
The cornerstone of any e-shop or website is hosting – a virtual space where your e-shop is stored. It is important to choose a truly reliable hosting provider that will protect you from internal and external infrastructure attacks and keep up with the latest security trends. Learn about monitoring and preventing attacks, regular updating and fixing security vulnerabilities, or the possibility of the preventing spread of infected files in the network after being attacked.
The more demanding of you may also be interested in hosting your own server, which can be additionally secured by your own encryption, or by the country where the servers are located (due to privacy laws). Ideal destinations are Switzerland, Sweden or Iceland.
The firewalls and their capabilities also present an important aspect of security. If the provider cannot provide you with adequate protection, consider your own hosting. When setting up, we definitely recommend consulting with security experts.
-
Choose a secure CMS system
When creating an e-shop, as well as safe hosting, the choice of a trusted CMS system is also important. When selecting the right solution, consider several parameters, such as the programming language in which the CMS system was created. One of the main reasons why you choose a CMS system should be its security and openness (open source project). When choosing the right CMS system, CSM Martix site might be helpful.
While the world’s largest CMS system is WooCommerce based on WordPress, many experts say CMS system Magento is safer. It is also used by Nike, Coca-Cola, Nestlé or Burger King. Drupal and RefineryCMS, e-commerce platforms OpenCart, Shopify and PrestaShop are also worth mentioning.
-
New Feature = New Threat
It is natural that every e-shop and web has to evolve over time. With new features, however, new threats also come. When implementing new features in your e-shop, you should choose the top priority of their security so that by adding a new feature, you don’t risk compromising the security of the entire system.
Security should always be priority number one for you.
Increased attention should be paid to various “third parties” as well as to the “proprietary” plug-ins and complements to CMS systems, which are separate elements of the system with insufficient level of protection. These are often the source of various security bugs and vulnerabilities through which the whole page can be hacked. (Hacktrophy focuses on the ethical search for them.) It is also important to regularly update and track changes that may occasionally bring a new kind of vulnerability.
If the plug-in you chose does not receive regular updates, take a look at its alternative or talk to developers about the possibility of more regular updates with bug fixes.
-
Security plug-ins for CMS systems
If you chose the CMS WordPress to run your e-shop or website, you can increase your security by using security plug-ins. Their offer is really rich today, so we select a few plug-ins that should not miss your attention:
If you choose a different CMS system, learn about installing add-ons that can improve your security. Whether it is a basic Captcha system or more complex solutions, such as protection against DoS and DDoS attacks. You can also make a significant increase in the security of your CMS by deploying WAF (web application firewall), such as mod_security on the web server (Apache, NGINX).
A good CMS system should be actively involved in this topic and communicate it to its users.
-
Integration of Third Party Services
A separate chapter that deserves your attention is the integration of third-party services. The conscientious choice of the payment gateway is of particular importance. It should be localized into Slovak language and provide sufficient security.
We also recommend that you choose a payment gateway that processes customer data separately and ultimately offers you only information about your payment success. In this case, you will, to a certain extent, transfer the legal responsibility for your customers’ payment information to the payment gateway operator, and you do not have to deal with PCI DSS audits that are time consuming and costly.
5 Steps to Properly Choose a Payment Gateway:
1. Internal or external
Decide whether you want to operate a payment gateway directly in your e-shop or use it as an external service. Each of these solutions has its pre and counter. The biggest drawback of the internal solution is the already mentioned PCI DSS audits (more in point 5).
2. List of features and integration options
Make sure that you can integrate the payment gateway into your CMS system. Also focus on the features it offers – type of supported payment cards, payment via PayPal services, or payment in cryptocurrencies. As a merchant, you should also be interested in payment statements, the payout period after the transfer of money to your account, or the administration options.
3. Fees
Some payment gateways charge the percentage of the amount transferred, others offer fixed fees for all types of payments, and some payment gateways operate on a monthly basis. Choose the type of payment gateway that best fits your business type.
4. Support
Though many traders do not think so, the support from the payment gateway provider is really important. Best if it is provided 24/7 and in a language that you know.
5. Security
Each secure payment gateway should accept the PCI standard. This defines a set of rules and responsibilities that you need to follow when working with the payment cards. When selecting a payment gateway, you should also get informed about the security updates and the additional protection offered by the payment solution.
-
Avoid the most common vulnerabilities
Your e-shop may contain a number of vulnerabilities that can be misused by black hackers. OWASP statistics include, in particular, the insertion of unwanted (SQL) code, poorly-crafted “uploading”, erroneous identity verification, and ongoing XSS vulnerabilities and sessions.
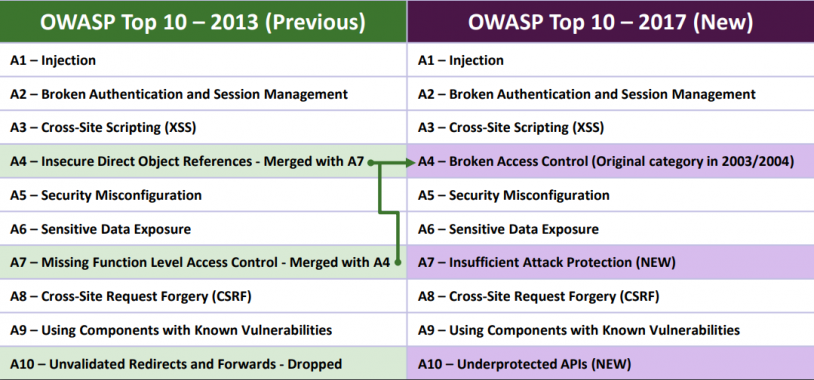
TOP 10 most common website security vulnerabilities by OWASP.
There are several options to protect yourself from inserting SQL code, as well as from cross-site scripting attacks. However, protection should be as universal as possible, and you should not only focus on a few types of hacker attacks.
We know two general approaches to filtering dangerous content:
- Blacklisting – in principle, allows all types of connections, detects and filters only dangerous inputs. For web application security and access to the e-shop administrative environment, this is not recommended.
- Whitelisting – works by allowing only certain types of connections (inputs) and all other connections are blocked (firewall principle). This approach is recommended for online security and should replace the blacklisting approach, at least in the administrative part of your solution,
-
Settings of limits and security rules
Although human being – a black-hat hacker – is always behind the virus or infected file, their spreading is automated in the vast majority of cases. Computer scripts and self-running robots are looking for an endless way to infect as many files as possible on your site.
However, setting limits and safety rules can reduce the likelihood of your system infecting. In this case, you need to focus on the network portion of your online solution and reduce suspicious connections and repetitive network requests of the same type. Application firewalls can be used for that. Of course, the many times mentioned sensitive data deserve separate protection.
When making safety rules in your company, the US Federal Trade Commission can serve as a good example. In the general safety guidelines, it provides 5 basic steps:
- Analyze: Find out what type and volume of sensitive data you store in your servers, systems, and the of staff’s personal computers.
- Scatter: Keep only the data you really need in your business.
- Lock: Securely protect all the data you have chosen to save on your system.
- Check and Delete: Discard any data that is outdated or no longer needed in your business.
- Plan: Plan how to handle your data in case of expansion. Also plan the steps you will take if you lose some of your data. Be predictive and ready for every situation!
-
Encrypting
Today, it’s a must for your site to offer an encrypted connection. The basis is an SSL certificate that provides encrypted user connectivity when they are on your site or e-shop. HTTP protocol wrapped in secure SSL / TLS connections (HTTPS) gives the impression that their communication with you is safe (not always guaranteeing the security of the solution). And if the customer thinks he’s safe, he’ll be more likely to shop with you and there’s a bigger chance that he’ll be back in your e-shop in the future.
If your customers get the feeling that they’re shopping in a secure e-shop, they will be more likely to buy in your e-shop in the future.
-
Back up
Backup is a recommended practice not only in the area of web sites and e-commerce. It is a basic pillar of security as such, and offers the option of returning your system to its original state after a hacker, an aggressive virus or a software or hardware component fails. If you have not backed up your data yet, you should start immediately!
-
Regular updates
If regular updates of operating systems on your devices seem to be superfluous, the opposite is true. The vast majority of automated hacking attacks should be radically smaller in the case of the updated system, or would not be successful at all. Make sure you always use the most up-to-date version of the operating system and all of the applications and services that are used, which can, in addition to new features, often fix critical security vulnerabilities.
-
Protection against DoS and DDoS attacks
Cloud-based services, such as Cloudfare, can work as universal protection. They act as mediators of security solutions for online services of different types. In addition to improving website performance, they also offer protection against DoS and DDoS attacks as well as other types of attacks. This is primarily an external web traffic filter that eliminates attacks before they reach the level of your e-shop or website.
Internal protection against these types of attacks may, however, become the already mentioned WAF (for example, mod_evasive modul, which is explicitly targeted against DDoS attacks). Its advantage is finance, because it is a solution for which you don’t have to be pay regularly to anyone.
-
Company password policy
Passwords from an e-shop administration perspective
For enhanced protection of your site, you need to use a strong password that requires several rules to be created. The password must be long enough, it should not contain your name and surname, it should contain both upper and lower case letters, numbers and characters.
In general, however, the complexity and therefore password strength grow exponentially with its length, so it is recommended to use a longer password phrase that you can easily remember but is not directly connected with you or the company. It is also recommended that you do not write your password on paper that you then stick to your computer monitor or put it in your wallet.
You can check the power of your password through multiple tools (such as the Passwordmeter).
Strong password is the basic security element of the administrative part of your e-shop, as well as the access part from customers.
In addition to a strong password, we strongly recommend using the so-called 2-step authentication that verifies identity beyond the password by sending an SMS message or generating code from a special mobile application.
Passwords from e-shop customer’s perspective
We also recommend that you support the most secure password policy on the client side, including the double-factor authentication mentioned. It is important that your system does not accept overly easy user passwords, passwords associated with login password, and passwords that are in the list of most frequently used passwords. In WordPress you can also use the Force Strong Password plugin.
Anonymization is also important. Instead of “Incorrect username” or “Incorrect password”, the system should write “incorrect login” or “incorrect username or password”. Then the attacker will not know which part of the authorization pair is wrong.
Of course, limiting the input of incorrect login data should also be a matter of course. One option is temporary denial of login for a period of time (for example, after 5 incorrect attempts, one can not be logged for an additional 15 minutes), or temporarily blocking the account after entering incorrect login data by X times, until the identity of the user is additionally verified.
-
VPN protection
An extra level of protection for your administrative interface can be a combination of IP address restriction and VPN connection, or TLS connection with the necessary use of client’s TLS certificates. Separate connection encryption, which can only be done from your PC, almost eliminates the ability to track communication between your PC and corporate systems.
VPN connection can also be used to sign in to sensitive content sites through untrusted networks or from abroad. In this way, you can, to some extent, also protect employee access to the administrative interface of your e-shop via unsecured Wi-Fi networks in holiday resorts or airports.
14. Penetration tests and security audits
Penetration tests are a one-time test of computer system security. They simulate a massive cyber attack and highlight security flaws that could lead to data leaks and misuse, or to your e-shop’s malfunction. Testing by so-called pentest is recommended when launching a new website or e-shop as a first step towards achieving greater security of the solution.
Like a penetration test, a security audit is also a crash test for potential threats. It examines whether the company and its system are subject to rigorous security rules and what steps they should take to comply with them in case of finding a deficiency. For example, companies such as Citadelo, Nethemba or Eset are performing pentests and audits.
-
Testing e-shop security with ethical hackers
Another option for testing e-shop security is so-called bug bounty program, such as the European Hacktrophy or American Hackerone and Bugcrowd. You can read about its importance in a separate article. The advantage of bug bounty programs is that you only pay for vulnerabilities that ethical hackers will actually discover in your system. Compared with penetration tests, this type of testing is usually cheaper and more continuous – the community of ethical hackers is testing your security for long time and for pre-defined rewards.
Pentest offers a one-time e-shop security test at a given time. A bug bounty program provides continuous testing in collaboration with hundreds of experts.
Engaging a bug bounty program can be done either after or without a penetration test – for example, when you program a new feature that may include security bugs in the e-shop. If you do not have enough money to conduct a security audit, Hacktrophy is the ideal solution.
16. Following the trends
If your product’s security is handled by an internal team of specialists or you yourself, we also recommend that you keep track of online databases of known vulnerabilities by software or CMS that you use (such as Exploit Database, OSVDB or CVE). Here you can find information about threats that also affect your system. Appropriate resources that are also worth watching include, for example, The Hacker News or Stop The Hacker.
Interesting articles and information about online threats involving Slovak and Czech companies can also be found on our blog on IT security.
17. Educate your employees
Up to 32% of all data loss cases are the consequence of human failure. That’s why it’s a constant necessity to educate you and your employees about online security. Courses and trainings of this type are offered by the Slovak companies Nethemba and Citadelo.
In addition to training, a strict security policy for employees is also required in your company. It should limit the conditions for the use of private facilities, restrict the use of social networks over working hours, or set strict rules for dealing with sensitive data.
All your employees are responsible for the security of your e-shop and sensitive customer data.
Infringement of these rules would, according to the new data protection standard (GDPR), might cost your company a lot – in extreme cases you will be fined € 20 million or 4% of annual turnover.
A security policy for employees can be a part of their employment contract. This will prevent data leakage and unnecessary problems that could be caused by your employees’ irresponsibility. For projects with greater financial value, it is more appropriate to “employ” self-employed or private companies with whom it is possible to agree liability for damages using the NDA or other contract of this nature.
18. Educate your customers
Each coin has two sides and although you can secure your e-shop the best you know, you still can not avoid all security incidents. It is important that you speak publicly about safety and educate your customers. Explain why you do not accept simple passwords, why you use 2-step authentication, and what security measures you do on your site. Check it out and make your e-shop more trustworthy.
19. Legal aspects of e-commerce business
When doing business on the Internet, similar rules to legal issues apply as in the case of classical business. It is therefore necessary to develop a security project that includes a security plan, an analysis of the security of the information system, as well as conclusions on the security plan and IS security analysis.
If you are not sure what all the documents you need to create when setting up an e-shop, consult your lawyer. But think about it before you launch an e-shop to avoid fines on state authorities or trade inspection.
20. Intellectual Property and Trademarks
Although the subject of intellectual property protection affects the safety of your e-shop only marginally, you should not miss it. Even before you start your e-shop, register your logo and the name of your e-shop. This will prevent potential problems with creating copies of your e-shop by malevolent people.
One of the most precious commodities you trade with in today’s world is your reputation. It’s the last thing you want to deal with, to make it damaging to someone from your competition by copying your e-shop and acting on your behalf and spoiling your reputation.


