The first Central European bug bounty program, Hacktrophy, is celebrating a year of existence. Building a service of this kind in the heart of Europe hasn’t been an easy task. We decided to proactively educate companies about the importance of online security testing and to get in touch with community of ethical hackers (not only) from our region.
Challenges and obstacles to ethical hacking in Central Europe
Creating a platform for bug bounty projects in Central Europe has brought several challenges. First of all, the very idea of working with ethical hackers is a problem for many. We also came across the fact that sometimes even the security experts did not know this form of IT security testing and were sceptical about it.
Therefore, to clarify how a bug bounty project works and why companies should use it takes us a lot of time. The awareness that really every company is a potential target of a cyber attack, so the level of IT security mustn’t be underestimated, is still insufficient in our country. That’s the reason why we chose the way of education, whether by presentations of dozens of professional events or blogs.
When a company had decided to go to the bug bounty project, the discussion of its character as well as the subsequent detailed setup was a big challenge. It sometimes takes several weeks or months. The situation is complicated by, for example, complex decision-making processes in companies and the technical requirements that need to be provided for bug bounty programs (testing environment, special hacker accesses, list of testing exceptions, etc.).

Source: ccpe.kennesaw.edu
Practical experience with creating and managing bug bounty project
When creating a bug bounty program, we must take into account the client’s security testing experience, previous penetration tests, the specific product or service requirements, the nature of sensitive corporate data, and last but not least the test budget.
The most difficult decisions for businesses include the right amount of rewards for ethical hackers. This is due to the lack of experience and the amount of funding that society pays for security testing. Very few Czech or Slovak companies invest recommended 5% of the budget for development in its security. We are therefore actively helping companies to set optimal rewards, as well as other bug bounty parameters.
From our experience, we know that the problem lies also in the repair of the vulnerabilities found. Companies are primarily committed to serious vulnerabilities, and their repair often takes too long, putting us in an uncomfortable position against hackers themselves. On average, it takes several weeks for the company to mark the vulnerability as corrected. Without changing the status of it, we and the hacker who reported it can’t check the validity of the repair. In Hacktrophy, we pay hacker rewards only after the problem is eliminated, so we need to communicate appropriately in bug bounty projects if the company does not have the capacity to quickly fix the vulnerabilities.
Together with our clients, we learn how to make the most effective communication between moderators who are their extended hands and ethical hackers. We are looking for an effective way for a company to get the least burden on the project itself, but not to get rid of any important information. It starts with the normal distribution of notification emails and ends with the possibility of a private chat with the assigned moderator.
Rewards for hackers, new website and pricing packages
Our platform has so far paid out rewards in three currencies – Czech crown (CZK), Euro (EUR) and Bitcoin (BTC). Our communication shows that ethical hackers prefer payments in euros.
During the first year of our operation, we received a feedback from our clients that allowed us to understand what information is relevant to clients and what pricing model they favour. As a result, we redesigned our website and created a new pricing model – we have the new Hacktrophy packages and for the demanding clients we also have the option of setting up the package by themselves.
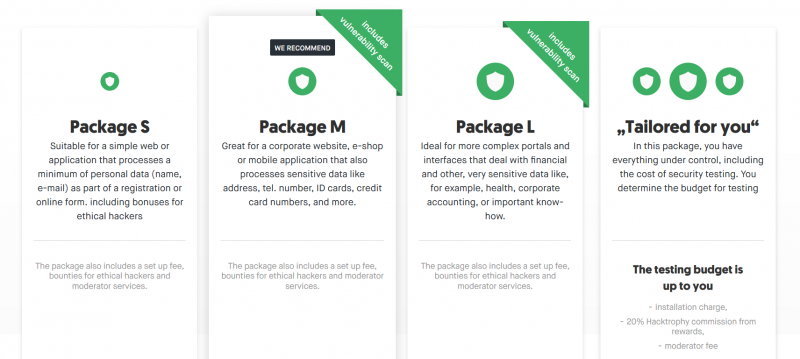
Hacktrophy packages allow businesses to better set their security testing budget by directly seeing what their money is used for. At the same time, we can openly declare that our services are still significantly cheaper than similar platforms abroad.
Ethical hackers can save companies a tens of thousands a year
Despite the short time horizon, we have succeeded in achieving several milestones that we are proud of. More than 450 hackers have joined our community in a year. More than 70% of them are ethical hackers from Slovakia and the Czech Republic. One of the challenges we face is the expansion of Hacktrophy and hiring specialists from other countries.
Security testers have reported to Hacktrophy companies more than 200 vulnerabilities of their online systems, out of which 78 vulnerabilities have proven to be valid. 15 of the valid vulnerabilities represented a high risk of attack.

Ethical hackers earned almost EUR 10,500 for the year of our platform, with the highest one-time hacker reward of 1238 EUR. However, companies, thanks to correcting these security vulnerabilities, saved theoretically up to ten hundred thousands euros that they could lose as a result of black-hat hacker attack.
Professional eye of the moderator
The bug bounty projects of our clients are taken care of by moderators, the qualified IT security specialists. One of them is Roman Fülöp, who presents his insight into the results of Hacktrophy testing:
Results show several possibly interesting metrics. First of all, the percentage of valid (approved) issues was less than 40%. This means more than 60% of false positives, out-of scope reports, duplicates or reports rejected for other reasons. This e.g. shows the fraction of effort a moderator can save.
Customers usually define a group of issues that they consider to be of acceptable risk. This is mostly debug information, information leaking via HTTP headers, error messages etc. Data shows that even though there is no reward for this class of issues, hackers tend to report them – not only they consider it to be ethical but also it builds up their reputation.
Majority of vulnerabilities rated as low consisted of various SSL/TLS related issues. This may be caused by several causes – developers and administrators are still not greatly aware of mechanisms that supplement SSL/TLS encryption such as lack of cookie flags or HSTS, but also the rapid development and appearance of new issues on SSL layer. Protocols, cipher suites, key strength and other parameters which were sufficient a year ago most probably aren’t today.
Amongst medium and highly rated vulnerabilities there is nearly a tie between IDOR (Insecure Direct Object Reference) or horizontal privilege escalation, various XSS (Cross-site Scripting), CSRF (Cross-Site Request Forgery), and session fixation. While it is sometimes easy to omit tight authorization checks, input/output validation and CSRF protection is nowadays present out-of-the-box in many development frameworks – but nevertheless XSS and CSRF still appear. Even the single reported critical vulnerability – vertical privilege escalation – was discovered by exploiting a blind stored XSS in administration interface.
Other critical issues such as LFI (local file inclusion), RCE (remote code execution) and SQL injection were not reported at all. Given that nowadays hopefully nobody writes SQL queries by hand, this is expected.
At last, it is worth mentioning that there were many reports regardinglack or misconfiguration of SPF (or other similar mechanisms) – and even though infrastructure problems are usually out of the testing scope, customers were interested in these as the possibility of forged e-mails possibly resulting in phishing or reputation loss seem riskier than it seems on first glance.)
(If you did not understand the terms Roman used in his summary, please read our Basic Vulnerability Description.)

What are the news?
This year, we successfully integrated the 2-factor verification (2FA) into Hacktrophy, added options for setting annual reward limits (monthly limits available from scratch), hacker recommendations to correct reported vulnerabilities, expanding email notification options for individual processes within the project, but also the ability to pay rewards to hackers in countries other than the euro. But we definitely do not stop with improvements.
We are currently working on creating a rating system for ethical hackers. It will help us deal with reporting of fake vulnerabilities. You will also benefit from the system in private bug bounty programs, where, on the basis of the rating, you will be able to invite the relevant testers.
Last but not least, we are working on improvements to the design and usability of our application and website. The new design that we updated on the web just weeks ago now offers more practical information not just about Hacktrophy.
In addition to educating our clients, we want to continue to bring security news and useful hacker topics to the future. We want to build a community that understands modern security testing trends and understands that security is a basic condition to the development and sale of any product or service. Do you want to be part of our project? Do not hesitate to contact us.
Roman Jazudek, CEO Hacktrophy


